Inside France's Massive Defense Data Breach: Exposed Naval Secrets and Cybersecurity Risks
France Reels as Massive Data Breach Exposes Advanced Defense Secrets
An Unprecedented Incident Hits National Security Core
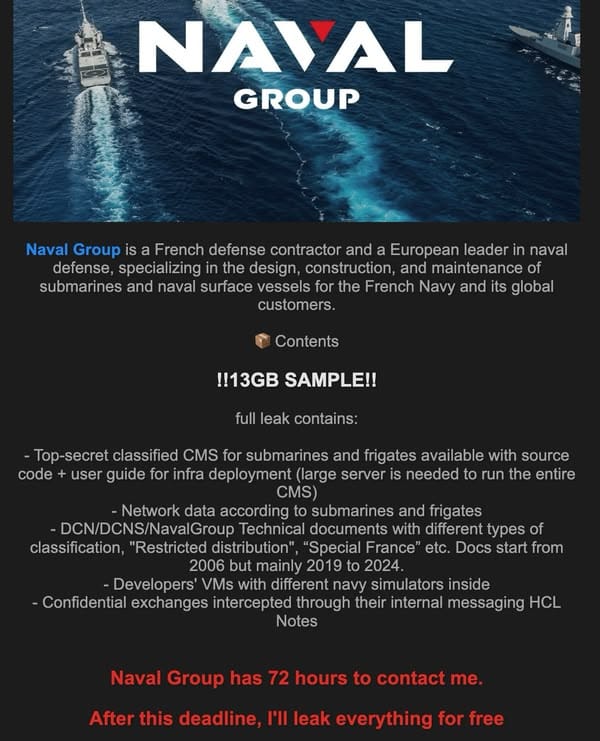
A landmark cyber event has sent shockwaves through France's defense sector, as a prominent European shipbuilder confirmed a significant leak of internal data. Reports indicate that the organization, renown for supplying advanced surface vessels and underwater platforms, has come under scrutiny following a wave of digital intrusions. This breach centers on highly confidential engineering documents and operational frameworks used in some of Europe’s most sophisticated maritime assets.
Investigations reveal that the compromised archive includes source code fundamental to complex systems that manage onboard weaponry and critical control sequences for strategic platforms. Additionally, the leak reportedly contains engineering details for military aviation programs and a cache of sensitive correspondence between key executives. Industry observers note that the exposed materials extend beyond European navy projects, with claims emerging about data also touching on American fleet management systems.
The organization at the center affirms ongoing coordination with national authorities and specialized cyber investigation teams. In initial statements, company representatives emphasize strong action to assess the extent, origin, and integrity of the disclosed information, while also highlighting the lack of direct evidence of internal operational disruption. This multi-layered response reflects the modern challenges of tracing digital infiltrations in an era where supply chain complexity intersects with evolving cyber risks.
Critical Materials at Stake: What Was Targeted?
Central to the incident is the alleged exposure of combat operation source code, which underpins the logic behind how maritime defense platforms function during both drills and real engagements. The ability to simulate, control, and respond to threats forms the backbone of any modern vessel’s defensive and offensive postures, making such code foundational—not only from a technical standpoint but for national sovereignty as well.
In addition, frameworks connected to underwater capabilities were reportedly compromised. This includes the digital architecture that directs advanced underwater assets, particularly systems governing the deployment of special payloads. Retaining the confidentiality of these electronic blueprints is crucial, given the immense investment and research underpinning their development.
Confidential blueprints and user guides for military aerospace assets are also part of the leaked data. Such documents integrate system specifications and performance parameters, essentially serving as a digital map of technological strengths and limitations. Communications between high-ranking staff, if genuine, potentially offer insights into strategic decisions and operational hierarchies within the organization, which are of significant value for industrial and geopolitical analysts.
Implications, Verification, and Strategic Response
The digital materials, totaling a substantial dataset, were distributed by individuals operating under pseudonyms within highly restricted online communities. The method of publicizing the breach—initially via a sample, followed by a significant dump of files—has mirrored trends observed across other high-impact information disclosures. The actors involved have stated their intentions included drawing attention and applying negotiation pressure, though no direct financial demands have been openly documented in this instance.
French government agencies, alongside global security counterparts, have instituted thorough audits to validate the authenticity and scope of the dispersed materials. The gravity of the breach derives not only from the size but from the nature of the information, capable of influencing technological advantage, operational security, and market confidence. Cybersecurity teams are cross-referencing digital signatures and content fragments to ensure accuracy in cataloging what has and has not been exposed.
The organization at the heart maintains that its operational networks remain uncompromised, framing the event as an effort to damage reputation and provoke uncertainty in ongoing and future initiatives. Nonetheless, this situation highlights vulnerabilities that impact not only the host entity but allied enterprises and associated governments. The dialogue around this event extends to the reliability of interconnected partner programs, the transnational flow of sensitive information, and the long-term processes required for remediation and trust rebuilding.
Conclusion: Redefining Security in an Interconnected Defense Ecosystem
As verification efforts proceed, this high-profile breach underscores the persistent evolution of cyber risk within industries tasked with protecting national interests. The alleged disclosure of system software, command frameworks, and internal deliberations encapsulates the stakes faced by contractors supporting maritime, aerial, and allied operations worldwide. Security strategies are being rapidly re-examined, with robust incident response mechanisms now more critical than ever for the integrity of industrial and defense innovations.
Such a landmark event will likely recalibrate the benchmarks of digital resilience in sectors where confidentiality, technical edge, and reliability are paramount. Ongoing investigations and transparent disclosures will determine the ultimate impact, shaping how security postures are prioritized in an ever-shifting electronic landscape.
